The 5 most dangerous Wi-Fi attacks, and how to fight them

 Image: deepadesigns / Shutterstock.com
Image: deepadesigns / Shutterstock.comAn attack on your Wi-Fi network is not like a bank robbery: Instead of masked robbers blowing open the vault with a loud noise, a hacker inconspicuously approaches the router, searches for weak points and tries out several attack paths. Or he exploits a known security hole by unleashing an attack on the router that has been prepared for this purpose.
Because you never know when and where your router will become a target, you should always ensure that the device is protected against hacker attacks: Increase the protection level of the router with suitable settings so that an attack is too costly for the hacker. And keep yourself regularly informed about security gaps so that you can plug them with firmware updates.
We show you how the most dangerous Wi-Fi network attacks work and how you can protect yourself against them: This means you immediately have the right answer to hacker attacks at hand and can secure your router and home network in just a few simple steps.
Further reading: How to secure your home Wi-Fi network and router
Why hackers attack your Wi-Fi network
To attack a Wi-Fi network, hackers either attack the Wi-Fi connection between client and router or they attack the router directly.
With the first strategy, the attackers want to record data that the devices exchange via Wi-Fi: In this way, they can first guess the Wi-Fi key in order to then connect to the connection or redirect it. In this way, they gain access to sensitive information such as passwords for online banking or online accounts. They can then use these themselves or sell them to other hackers.
In addition, attackers can go online via your internet access to download copyrighted material, for example, or to carry out other criminal acts that cannot be traced back to the hacker, but only to you.
If attackers take over the router, all devices in the network are open to them: They can, for example, manipulate smart home devices that control lights, heating, or the alarm system. In addition, they can reach data on computers or NAS devices in this way, which they encrypt via ransomware in order to extort a ransom.
In most cases, a hijacked router becomes part of a botnet that hackers use to attack other targets, such as internal networks of government agencies or companies. But even if an attack has less ambitious goals, it can be annoying: For example, a neighbor who has the fun of disrupting your network and online connections with a Wi-Fi attack. Or family members who hope to override parental control settings or website filters by gaining unauthorized access to the router.
Deauthentification: The first attack on the Wi-Fi network
Deauthentification is one of the standard attacks against the Wi-Fi
network: How and with which tools hackers proceed is described in detail on numerous websites.
Deauthentification is one of the standard attacks against the Wi-Fi
network: How and with which tools hackers proceed is described in detail on numerous websites.
IDG
Deauthentification is one of the standard attacks against the Wi-Fi
network: How and with which tools hackers proceed is described in detail on numerous websites.
IDG
IDG
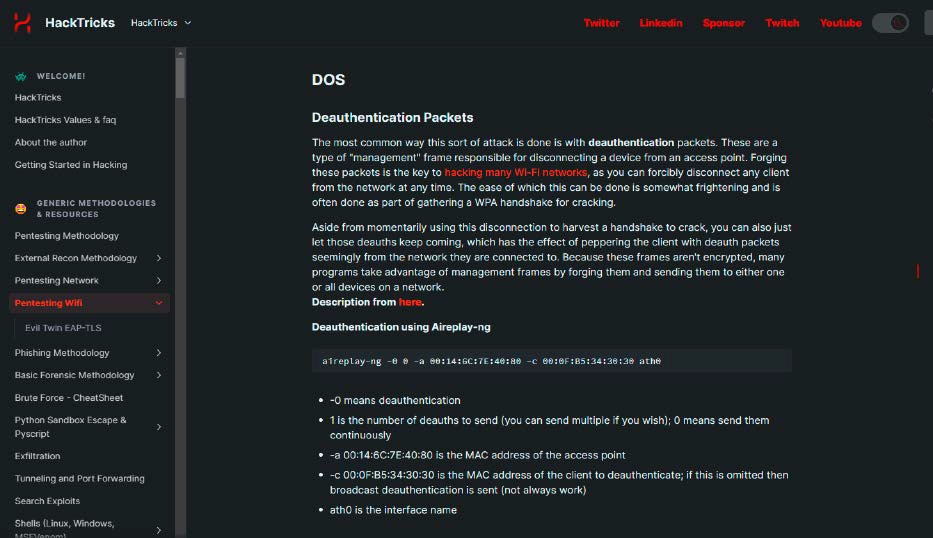
This is how the attack works: With a deauthentication, the hacker interrupts the connection between the router and a client. This logoff process is a common and standardized procedure in WLAN: A router, for example, sends a deauthentication message to a client that has not been active in the Wi-Fi network for some time, so that it does not have to maintain this connection unnecessarily.
With band steering or AP steering, the router can also forcibly deauthenticate a client so that it subsequently connects via a faster Wi-Fi frequency or with a repeater that provides it with a better Wi-Fi signal.
In the case of the deauthentication attack, the request to log off does not come from the router, but from the hacker. To do this, he manipulates a corresponding data packet: It contains the MAC address of the router and a client. In addition, the attacker must know the SSID of the attacked Wi-Fi network. If he also finds out the radio channel, the attack is even more targeted.
This is what the hacker wants to achieve: Deauthentication is the basis for most Wi-Fi network attacks. The attacker can, for example, interpose himself when the client wants to reconnect to the router after the forced logoff. The two devices exchange messages with which they confirm to each other that they know the agreed WLAN password without transmitting it directly. Then they define the keys with which the following data transfer is secured (4-way handshake).
With a suitable tool, the attacker intercepts the data traffic during the login, with which he tries to guess the Wi-Fi password. You can read more about how this is done in the section “Brute force attack” below. The Evil Twin attack also starts with a deauthentication attack.
However, the hacker can also permanently interrupt the connection between a client and the router (DoS, Denial-of-Service): To do this, he continuously sends deauthentication packets to the client, which therefore cannot reach the router. In a private network, smart home devices such as alarm systems or surveillance cameras can be paralyzed in this way.
How to fend off the attack: The deauthentication packets are not encrypted, so the attacker does not need a Wi-Fi or network password to send them, but only the Mac addresses and the WLAN SSID, which are easy to find out on a network.
You can prevent this by activating the Protected Management Frames (PMF) function: The easiest way to do this is with WPA3. PMF is a mandatory part of the current security standard. If you switch it on in the router, it also transmits the deauthentication packets with a common key so that the client knows that they actually come from the router it knows.
However, if the client does not support WPA3, this measure will not help you. However, PMF can also be used together with WPA2 on many routers: With the Fritzbox, for example, you can additionally activate PMF if you select the option “Activate support for protected logins of WLAN devices (PMF)” in the menu under “WLAN > Security.”
Brute force attack: How hackers crack your Wi-Fi password
A strong Wi-Fi password makes brute-force attacks more difficult because the hacker needs too long or too many computing resources to figure it out. Many routers will alert you to a password that is too weak.
A strong Wi-Fi password makes brute-force attacks more difficult because the hacker needs too long or too many computing resources to figure it out. Many routers will alert you to a password that is too weak.
IDG
A strong Wi-Fi password makes brute-force attacks more difficult because the hacker needs too long or too many computing resources to figure it out. Many routers will alert you to a password that is too weak.
IDG
IDG
This is how the attack works: All encryption in the Wi-Fi network derives the devices involved in a connection from the WLAN password they know. If, for example, after a deauthentication attack, the attacker cuts the data transfer to re-establish the connection, he can use it to deduce the password.
Usually, this does not happen directly after the interception, but the attacker unleashes a powerful computer with a strong CPU and GPU on the recording, which tries out different passwords in quick succession that could match it. He can speed up this process via an online service that uses several servers for this purpose. Dictionaries, databases with popular passwords, and character combinations serve as the basis for this attack.
In a masked attack, the attacker sets certain defaults that he believes match the Wi-Fi key — for example, that the first letter in the password is written in capital letters or that half of the password consists of numbers. This considerably reduces the effort required to crack the password: For example, guessing a nine-digit password in the form Anton1970 would take several years if the attacker had to try out all possible combinations of letters and numbers. If he speculates that the password consists of a name and a year, he will succeed in less than an hour.
This is what the hacker wants to achieve: If the attacker knows the Wi-Fi password, all doors in the home network are open to him. For example, he can infiltrate his own clients to gain access to other home network devices and shares. In addition, the entire data traffic can then be recorded without encryption.
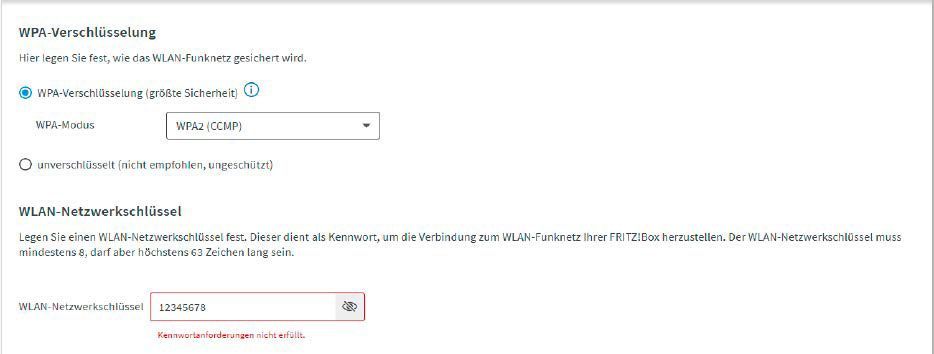
How to fend off the attack: The above example clearly shows that the longer and more complicated a password is, the more difficult it is to crack. Therefore, you should definitely avoid predictable words or numbers such as name, address, year of birth, etc. in your Wi-Fi password. Special characters also increase the complexity of the password. In this case, a shorter password with eight to 12 characters is sufficient, but its components of upper and lower case letters, numbers, and special characters are chosen completely randomly — for example z9!qO6+B§.
Also important: Do not use the password for another login, for example to an online account: If the provider of the account is hacked, the stolen passwords usually turn up quickly on the internet, and a network attacker can then use them for a brute force attack.
Further reading: Best password managers in 2023
Evil Twin: If the hacker places a false access point
Deactivate the automatic Wi-Fi login on a Windows notebook when you are in a public hot spot. This increases protection against an Evil Twin attack.
Deactivate the automatic Wi-Fi login on a Windows notebook when you are in a public hot spot. This increases protection against an Evil Twin attack.
Foundry
Deactivate the automatic Wi-Fi login on a Windows notebook when you are in a public hot spot. This increases protection against an Evil Twin attack.
Foundry
Foundry
This is how the attack works: You are particularly at risk for this attack in a public Wi-Fi network. But this attack is also possible at home. The hacker sets up a router or access point that uses the same SSID as the regular router. This can easily be found out via a network scan. An attacker can proceed in a similar way with a honeypot attack: To do this, he offers WLAN in a place that has no internet access, but where this is not immediately noticeable: For example, if he sets up a fake access point with the SSID “Pizzeria” in an Italian restaurant.
Both attacks can easily be carried out with a notebook or smartphone, as long as the client that connects can also access the internet via it. The attacker increases his chances of success if he places the false access point in such a way that it offers a better signal strength than the real one. He can also use a deauthentication attack to get clients to log off from the real access point and then connect to the fake one. With an unsecured Wi-Fi network, the hacker does not have to do anything else. If there is a Wi-Fi password, the attacker could present the client with a manipulated login web page when trying to connect in order to retrieve the password.
This is what the hacker wants to achieve: With the Evil Twin, the hacker can monitor the client’s entire data traffic — for example, the entry of passwords for online banking or shopping. Since this attack is usually not noticed immediately, the hacker has enough time to record enough data.
In addition, he gains access to the client to search for sensitive files or to install malware that gives him more possibilities to control the device.
This is how you can protect yourself: In principle, you should not do anything on a public Wi-Fi network that requires you to enter an important password. If this is necessary, you must make absolutely sure that you establish an encrypted connection to the corresponding site: You can recognise this by the fact that the web address begins with https://.
The best protection against attacks in a public Wi-Fi network is a VPN that connects you to your router at home: This encrypts all data that you send via the public WLAN.
Further reading: The best VPN services in 2023
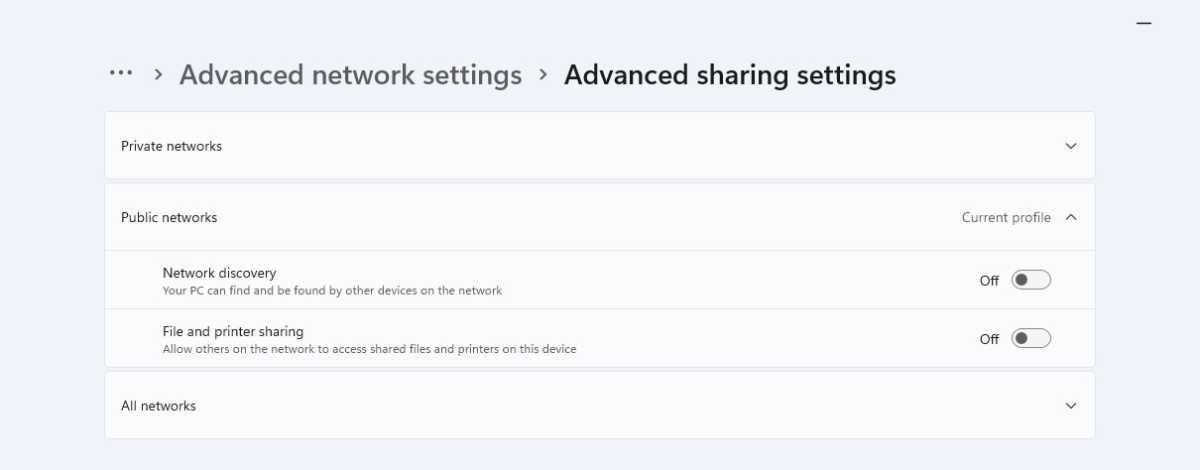
You should also avoid using Wi-Fi networks that do not require a password. It is also best to switch off the client so that it automatically connects to known WLANs: Otherwise, it will automatically contact every access point within range that uses a known SSID — even if it is a false one. Deactivate the automatic WLAN registration on a Windows notebook if you are in a public hotspot. This increases protection against an Evil Twin attack.
Router attack: How hackers exploit security gaps
This is how the attack works: The router is the most important device in your Wi-Fi network and therefore an attractive target for hackers. Many models facilitate these attacks through security gaps in the firmware: In most cases, it is based on Linux, which is why router manufacturers do not program all the functions themselves, but also rely on numerous open-source programs that may contain bugs.
In addition, some manufacturers fail to replace or remove from the firmware outdated firmware modules that are no longer maintained by programmers. These gaps allow attackers, for example, to have program commands executed on the router, as it does not check or filter these manipulated inputs. This can instruct the router to execute prepared scripts that give the attacker comprehensive control. Depending on the firmware gap, an attacker must be connected to the router via Wi-Fi or remote access to do this.
This is what the hacker wants to achieve: By means of a security hole, the attacker can completely take over the router in order to change settings or switch off security functions. In many cases, this serves to ensure permanent but unnoticed access to the router menu. The attacker can make the hijacked router part of a botnet with which he attacks other networks, for example, via a DoS attack or to send spam messages.
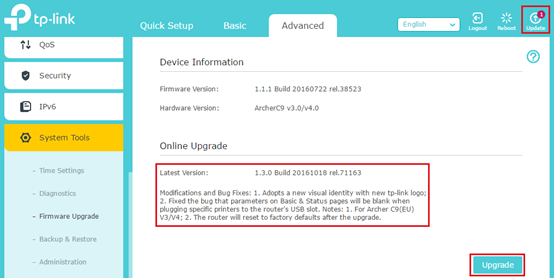
How to protect yourself: Regularly check whether new firmware is available for your router. It is also a good idea to regularly check important security websites that report on router vulnerabilities and to visit the support pages for your router model.
It’s important to keep your router firmware up to date. Some routers even offer a setting to automatically updgrade firmware.
It’s important to keep your router firmware up to date. Some routers even offer a setting to automatically updgrade firmware.
TP-Link
It’s important to keep your router firmware up to date. Some routers even offer a setting to automatically updgrade firmware.
TP-Link
TP-Link
Remote attack: Access to the router via the internet
This is how the attack works: Many users have set their router so that its settings can also be accessed from the internet. Therefore, hackers can also find these routers with a network scan, because remote access usually takes place via standard ports, such as port 443. Similar to cracking the Wi-Fi password, the attacker then tries to find out the access information — for example, via a brute force attack.
This is what the hacker wants to achieve: In the menu, the hacker changes settings that give him control over the router. In this way, he can integrate it into a botnet or redirect the online access of Wi-Fi clients to a manipulated server, for example, by storing corresponding DNS settings: In this way, passwords can be tapped or malware can be infiltrated into the home network.
How to protect yourself: It is best to activate remote access to the router only when you absolutely need it. It is absolutely important to have a strong password for logging into the router menu.
The router should also be able to offer to set up a user account for remote access that is different from the one for local access.
For additional security, an IP address range can often be defined: Only devices with a matching IP address can then access the router menu remotely at all. Many routers also lock the menu after a certain number of failed logins or extend the time period after each failed attempt until someone is allowed to log in again.
This article was translated from German to English and originally appeared on pcwelt.de.







