Update Chrome now to protect yourself from this zero-day exploit

 Image: Google
Image: GoogleAttackers have been exploiting a new major flaw in Chrome—the kind that can be used to run malicious code on a compromised device. Revealed last Friday alongside the release of an emergency fix, the vulnerability requires a patch that should be now available to most users of Chrome and other Chromium browsers (like Edge). This vulnerability is being exploited in the wild so you’ll want to update Chrome pronto.
If the update has already been pushed to your copy of Chrome, you should see a small notification in the upper right of your window (as will Edge users). Click on the button to apply the patch and restart the browser. Otherwise, follow these instructions to manually verify your browser version number and apply the patch:
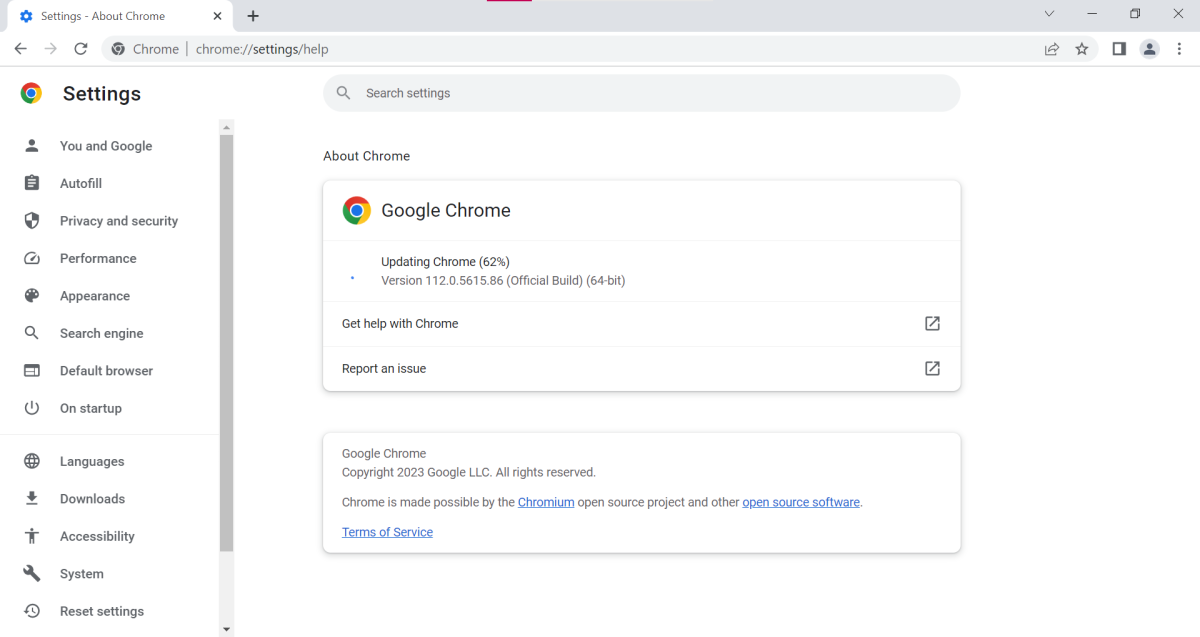
Chrome: Click on the three-dot settings icon on the far right of your menu bar. Then choose Help > About Google Chrome. You can also instead type chrome://settings/help into your address bar.Edge: Click on the three-dot settings icon on the far right of your menu bar. Then choose Help and feedback > About Microsoft Edge. You can also instead type edge://settings/help into the address bar.
PCWorld
PCWorld
PCWorld
If you’re not yet up to date, Chrome should automatically begin downloading the patch as soon as you open the About Google Chrome screen. You should then be updated to version 112.0.5615.121. Be sure that your version number matches the entire string—when we checked one of our PCs with Chrome installed, we were still on 112.0.5615.86, which meant the patch had not yet been applied. For Edge users, the same process applies, but the final version number will be 112.0.1722.48.
This exploit relies on a type confusion bug in Chrome’s V8 JavaScript engine, which we’ve seen in the wild before. This latest instance is the first one of 2023. Reported by Clément Lecigne of Google’s Threat Analysis Group last Tuesday, it affects Windows, Linux, and macOS. Details of how attackers have been manipulating this bug have yet to be unveiled, though, as is usual when a high-severity flaw is first uncovered. The delay of an explanation gives those affected time to apply the fix—which now you know to do.
Author: Alaina Yee, Senior Editor

Alaina Yee is PCWorld’s resident bargain hunter—when she’s not covering software, PC building, and more, she’s scouring for the best tech deals. Previously her work has appeared in PC Gamer, IGN, Maximum PC, and Official Xbox Magazine. You can find her on Twitter at @morphingball.
Recent stories by Alaina Yee:
AVG Internet Security review: Reliable, budget-friendly antivirus softwareWorried your inactive Google Account might get deleted? Log in nowBlack Friday 2023: How to get the best prices on tech, and where to shop




