An exploit can reveal your KeePass master password in plaintext

 Image: Michael Ansaldo/Foundry
Image: Michael Ansaldo/FoundryKeePass password manager users may want to be extra vigilant for the next several weeks or so. A newly discovered vulnerability allows retrieval of of the master password in plaintext, even when the database is locked or the program is closed. And while a fix is in the works, it won’t arrive until early June at the soonest.
(Update, 6/5/2023: KeePass version 2.54, which patches this vulnerability, is now available.)
As reported by Bleeping Computer (which covers the issue in full technical detail), a security researcher known as vdohney published a proof-of-concept tool that demonstrated the exploit in action. An attacker can perform a memory dump to gather most of the master password in plaintext, even when a KeePass database is closed, the program is locked, or the program is no longer open. When pulled out of the memory, the first one or two characters of the password will be missing, but can then be guessed to figure out the entire string.
For those unfamiliar with memory dumping vulnerabilities, you can think of this scenario a bit like KeePass’s master password as loose change in a pants pocket. Shake out the pants and you get nearly the whole dollar (so to speak) needed to buy entry into the database—but those coins shouldn’t be floating around in that pocket to begin with.
The proof-of-concept tool demonstrates this issue in Windows, but Linux and macOS are believed to be vulnerable, too, as the problem exists within in KeePass, not the operating system. Standard user accounts in Windows aren’t safe, either—dumping the memory does not require administrative privileges. To execute the exploit, a malicious actor would need either access to the computer remotely (gained through malware) or physically.
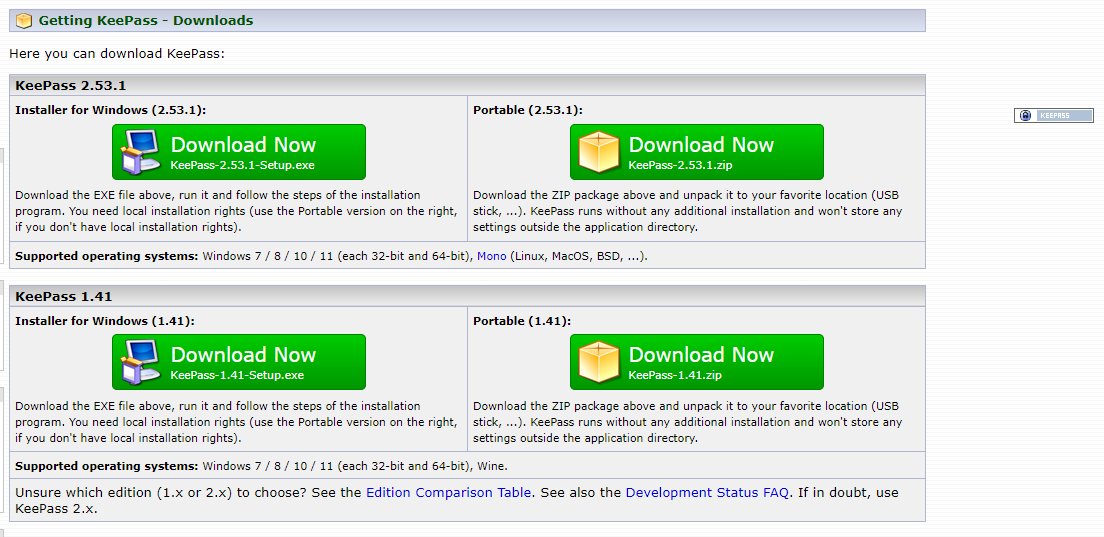
All existing versions of KeePass 2.x (e.g., 2.53.1) are affected. Meanwhile, KeePass 1.x (an older edition of the program that’s still being maintained), KeePassXC, and Strongbox, which are other password managers compatible with KeePass database files, are not affected according to vdohney.
A fix for this vulnerability will come in KeePass version 2.54, which is likely to launch in early June. Dominick Reichl, the developer of KeePass, gave this estimate in a sourceforge forum along with the caveat that the timeframe is not guaranteed. An unstable test version of KeePass with the security mitigations is available now. Bleeping Computer reports that the creator of the proof-of-concept exploit tool cannot reproduce the issue with the fixes in place.
However, even after upgrading to the fixed version of KeePass, the master password may still be viewable in the program’s memory files. To fully protect against that, you’ll have to wipe your PC completely using the mode that overwrites existing data, then freshly reinstall the operating system.
Our top Antivirus pick
Norton 360 Deluxe
 Read our reviewPrice When Reviewed:$49.99 for the first yearBest Prices Today:$19.99 at PCWorld Software Store | $49.99 at Norton
Read our reviewPrice When Reviewed:$49.99 for the first yearBest Prices Today:$19.99 at PCWorld Software Store | $49.99 at Norton
That’s a pretty drastic move, however. More reasonably, don’t let untrusted individuals access your computer, and don’t click any unknown links or install any unknown software. A good antivirus program (like one of those among our top recommendations) helps, too. When the fixed version of KeePass launches, you can also change your master password after upgrading—doing so should make the previous password irrelevant if it’s still lurking in your memory files.
You can also reduce your exposure by restarting your PC, clearing your hibernation and swap files, and temporarily accessing your KeePass database in a safe alternative like KeePassXC instead. Device encryption can also help against a physical attack on your PC (or if you think someone could mine this info after you donate or junk the PC). There are ways to stay protected—and fortunately, this appears to be only a proof-of-concept concern, rather than an active exploit.
Editor’s note: This article was originally published on May 19, 2023, and was updated on June 5, 2023 with a link to KeePass version 2.54, which patches this vulnerability.
Author: Alaina Yee, Senior Editor

Alaina Yee is PCWorld’s resident bargain hunter—when she’s not covering software, PC building, and more, she’s scouring for the best tech deals. Previously her work has appeared in PC Gamer, IGN, Maximum PC, and Official Xbox Magazine. You can find her on Twitter at @morphingball.
Recent stories by Alaina Yee:
Best antivirus software 2024: Keep your PC safe from malware, spyware, and moreMicrosoft says you should always ask this one security question to avoid scamsAVG Internet Security review: Reliable, budget-friendly antivirus software




