10 must-know PC security tips that keep you safe online

 Image: TierneyMJ / Shutterstock.com
Image: TierneyMJ / Shutterstock.comStaying safe online doesn’t mean having to learn coding or anything exotic. Germany’s Federal Office for Information Security recently published a brochure entitled “Using the internet safely” that contains ten helpful security tips that you should keep in mind while surfing the Internet to protect yourself from fraud and computer viruses.
The basic information is handy indeed, but we’ve expanded on these tips with recommendations on specific tools and security settings you can use to stay safe online.
Further reading: The best antivirus software for Windows PCs
Always keep Windows, browsers and applications up to date
Tip 1: “Set up your web browser securely and keep it up-to-date. Browser extensions should be disabled or uninstalled if necessary.“
Google Chrome, Microsoft Edge, and Mozilla Firefox check for available updates every time they are started and install them automatically. This applies to Windows as well as Android and iOS devices. Refrain from experimenting with alternative browsers from dubious manufacturers. These programs are often not carefully maintained.
the best password manager overall
Dashlane

 Read our reviewPrice When Reviewed:Free I Advanced: $2.75/mo I Premium: $4.99/mo I Friends & Family: $7.49/moBest Prices Today:$4.99 at Dashlane
Read our reviewPrice When Reviewed:Free I Advanced: $2.75/mo I Premium: $4.99/mo I Friends & Family: $7.49/moBest Prices Today:$4.99 at Dashlane
Even among the browser extensions in the manufacturers’ stores, there are quite a few candidates for which it is unclear what information they access and to whom they pass on this data. So you should install as few extensions as possible. For most users, the only thing that is almost indispensable is a password manager. These programs are now mostly offered in the form of browser extensions. Our guide to the best password managers can help you find a great one.
Tip 2: “Keep your operating system and other software up-to-date by allowing updates to be installed automatically.”
Windows, Microsoft 365, and many other applications have an automatic update mechanism that installs new versions and patches as soon as they appear. For all other programs, there are tools such as Sumo or the Iobit Software Updater that check the version numbers of installed programs and indicate available updates.
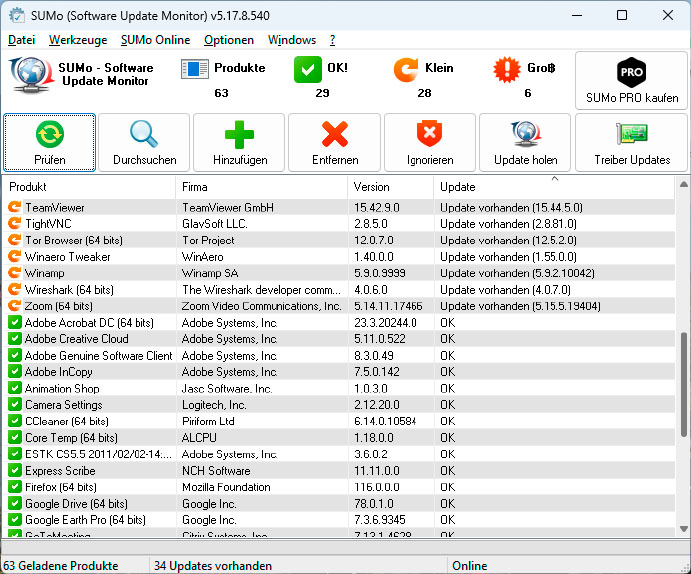
The update manager Sumo determines the version numbers of the installed programs and compares them with its database to detect outdated issues.
The update manager Sumo determines the version numbers of the installed programs and compares them with its database to detect outdated issues.
IDG
The update manager Sumo determines the version numbers of the installed programs and compares them with its database to detect outdated issues.
IDG
IDG
Tip 3: “Use applications for virus protection and a firewall. Some operating systems already offer such applications, but they must be activated.”
Windows includes virus protection and also a firewall, both of which are active by default, but they’re basic and aren’t very configurable. The best antivirus software suites include protect against threats like ransomware, phishing, and stolen identities.
Tip 4: “Create different user accounts and, if possible, refrain from using the device with administrator rights.”
Under Windows 10 and 11, you normally work with limited user rights. Even malware that has crept into the system only ever gets the rights that the current user has. It therefore does not have unlimited access to the system settings and cannot manipulate them. That’s why not using an admin account is one of our five easy tasks that supercharge your security.
If you need administrator rights, for example if a setup program wants to access the protected folders C:Programs or C:Programs (x86), the Windows user account control jumps in and asks you for permission. You can find it in the Control Panel in the icon view under “User Accounts -‘ Change User Account Control Settings”. For maximum security, set the slider to the highest level and confirm with “OK”.
the best windows antivirus software overall
Norton 360 Deluxe
 Read our reviewPrice When Reviewed:$49.99 for the first yearBest Prices Today:$19.99 at PCWorld Software Store | $49.99 at Norton
Read our reviewPrice When Reviewed:$49.99 for the first yearBest Prices Today:$19.99 at PCWorld Software Store | $49.99 at Norton
Tip 5: “Protect both your local user accounts and your online accounts with strong passwords. If possible, use two-factor authentication in addition.“
A secure password should be at least 16 characters long and consist of upper and lower case letters, numbers, and special characters. But again, you should really manage your passwords with a password manager and never use one password for multiple services.
With two-factor authentication, which is already mandatory for online banking and some other accounts, you create an additional hurdle for hackers and criminals. The authentication apps from Microsoft and Google have proven themselves as key 2FA options.
A newer technology called passkeys uses the cryptochips in smartphones or PCs serve as a secure key for services and make many passwords superfluous. Google, Microsoft, Apple, Amazon, and many password managers have already deployed passkey options.
Tip 6: “Be careful with mails and the attachments and links they contain. They are also used to infect devices with malware or to grab data.”
Phishing with fake emails is a preferred methods for criminals to spread malware and spy on access data. Either links lead to equally fake websites where you are supposed to enter your data, which is then tapped by the criminals, or an executable file is hidden in the attachment, which infects the computer with malware when opened. With the small, free add-in Attachment Scanner for Outlook, you can upload mail attachments with two clicks to Virustotal, a Google service that checks the files for malware with several dozen scanners.
For more help, be sure to read our guide on how to spot scam emails and texts.

Unsplash
Unsplash
Unsplash
Tip 7: “Be careful with downloads, especially if they are programs. It is best to download them via the manufacturer’s sites.“
Avoid websites that offer illegal versions of commercial software, such as software where the request for the license number has been removed, or cracks that allow you to skip authentication checks. That sort of software is often contaminated with viruses that immediately take root on your PC. Only download programs from trustworthy sources and scan the downloads with an antivirus program.
On that note, do not click on Google ads for antivirus downloads. They’re dangerous and often abused by hackers. Scroll down to the legitimate, organic search link instead.
Tools like Free Download Manager offer an option to automatically scan downloaded files. You can find the function in the program’s “Settings” under “Antivirus”.
Tip 8: “Be cautious about sharing personal data and only share it via encrypted connections (https).”
Social engineering is a method used by hackers for many years. The criminals obtain as much information as possible about a person and then try to get account data, passwords, or a signature from your victim via a fake email, SMS, or even by phone.
To prevent this, you should disclose as little information about yourself as possible when contacted. This applies especially to social media. Do not publish your private address or telephone number in generally accessible services, do not talk about your partner, children or other relatives, do not give bank details if possible, and keep your holiday details to yourself.
Tip 9: “When surfing, always make sure you have an encrypted connection (https). You can recognise it by a lock symbol or similar marking in the address bar of the browser.”
If you call up a website via an http connection, the data entered is transmitted unencrypted and in plain text, so that an intermediary hacker can read it if they’re on your network or they’ve breached the site you’re using. If, for example, an online shop appears on an http page, it is almost certainly dubious.
Chrome and Edge display http pages but mark them in the address bar with a preceding “Not secure”. Firefox contains a preset security mode that automatically switches to the https counterpart without prompting when an http page is called up. If no https version is available, the browser displays the warning “Secure website not available”. You will find the corresponding option in the “Settings” under “Privacy and Security” in the section “HTTPS-only mode”.
Tip 10: “Make regular backups on external storage media.“
the best windows backup software
R-Drive Image
 Read our reviewPrice When Reviewed:$44.95Best Prices Today:$44.95 at R-tools Technology
Read our reviewPrice When Reviewed:$44.95Best Prices Today:$44.95 at R-tools Technology
One of the biggest dangers for private users and companies are ransomware viruses. Hackers use them to encrypt your hard drive and demand a ransom for decryption. You can protect yourself with regular backups of your data on an external storage drive. (Here are the best external drives we’ve tested.) This must not be permanently connected to your computer, however, but should only be connected for the duration of the backup. Otherwise, if your computer gets infected by ransomware, your external drive might as well.
You can simply drag copies of your most important files over to the external drive if you want to keep things simple, but if you want a more full-featured option and the ability to take restorable “system images” of your Windows installation, check out our roundup of the best Windows backup software and best online backup services.
This article was translated from German to English and originally appeared on pcwelt.de.
Author: Roland Freist

Roland Freist bearbeitet als freier IT-Fachjournalist Themen rund um Windows, Anwendungen, Netzwerke, Security und Internet.
Recent stories by Roland Freist:
4 dangerous PC security exploits attacking right now (and how to fight them)Your email account was hacked. What now?What is a zero day exploit? The most dangerous security attacks, explained





